Most Common Method Used In Phishing Attacks are an enjoyable and engaging device for youngsters and grownups, offering a mix of education and entertainment. From tinting web pages and challenges to mathematics challenges and word video games, these worksheets deal with a large range of passions and ages. They assist enhance critical thinking, analytic, and imagination, making them optimal for homeschooling, class, or family members tasks.
Quickly accessible online, worksheets are a time-saving source that can turn any type of day into a discovering adventure. Whether you need rainy-day tasks or extra understanding devices, these worksheets give countless possibilities for enjoyable and education and learning. Download and install and appreciate today!
Most Common Method Used In Phishing Attacks

Most Common Method Used In Phishing Attacks
Welcome to The Multiplying 3 Digit by 2 Digit Numbers A Math Worksheet from the Long Multiplication Worksheets Page at Math Drills On this page, you will find Multiplication worksheets for practicing multiplication facts at various levels and in a variety of formats.
Free Multiplication Worksheet 2s and 3s Free4Classrooms

Cyber AI Archives Cyber Security News
Most Common Method Used In Phishing AttacksMultiply these numbers... ; 1, 2, 3, 4, 5 ; 6, 7, 8, 9, 10 ; 11, 12, 13, 14, 15. These worksheets have column form multiplication problems with 2 digit 10 99 and 3 digit 100 999 numbers
Enjoy these fall math fact sheets to practice multiplication facts. This document includes multiplication facts for 2 ' s , 3' s , ... Understanding A Phishing Attack 10 Types Of Phishing Attacks
Multiplication Facts Worksheets Math Drills

Understanding Different Types Of Phishing Attacks
This basic Multiplication worksheet is designed to help kids practice multiplying by 2 3 or 4 with multiplication questions that change each time you visit Phishing Attacks
This Multiplication worksheet may be configured for 2 3 or 4 digit multiplicands being multiplied by 1 2 or 3 digit multipliers Phishing Attacks Social Engineering
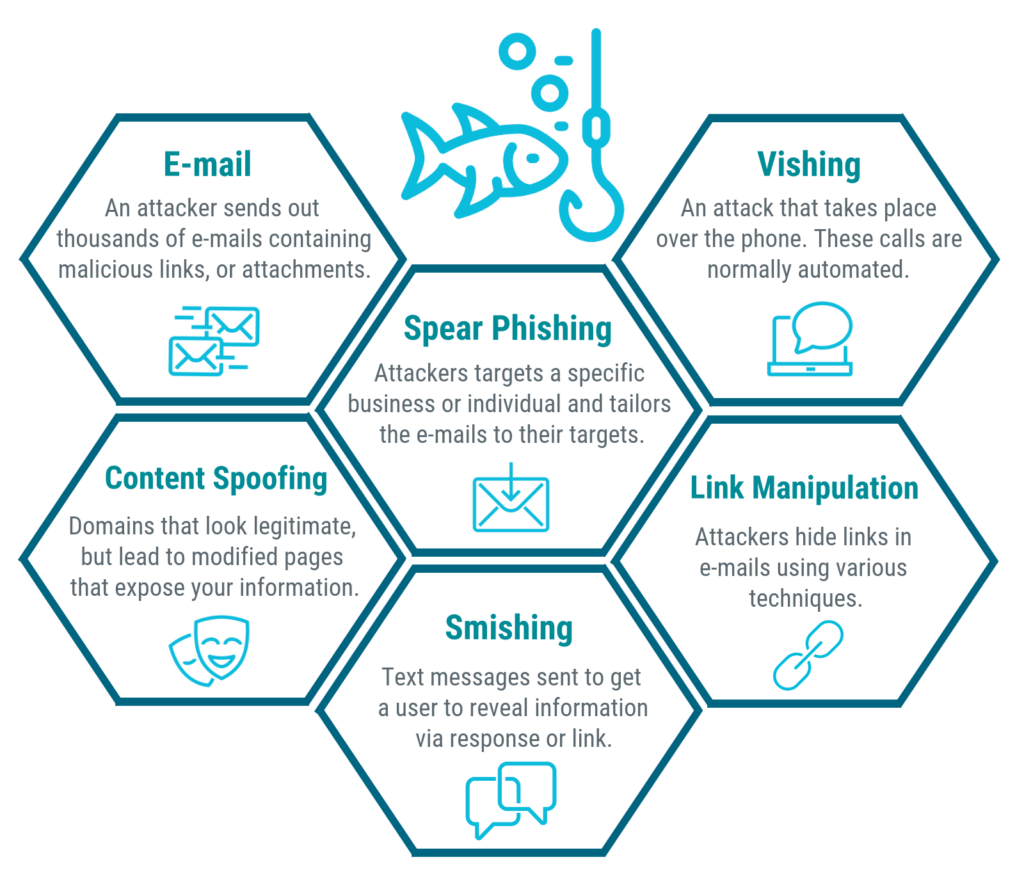
Phishing Characteristics Infoupdate

Phishing CyberHoot Cyber Library

Attack
Callback Phishing Attack Tactics Evolved Drops Ransomware

Different Types Of Welding Processes

Phishing Attacks

Phishing Attacks
Phishing Attacks
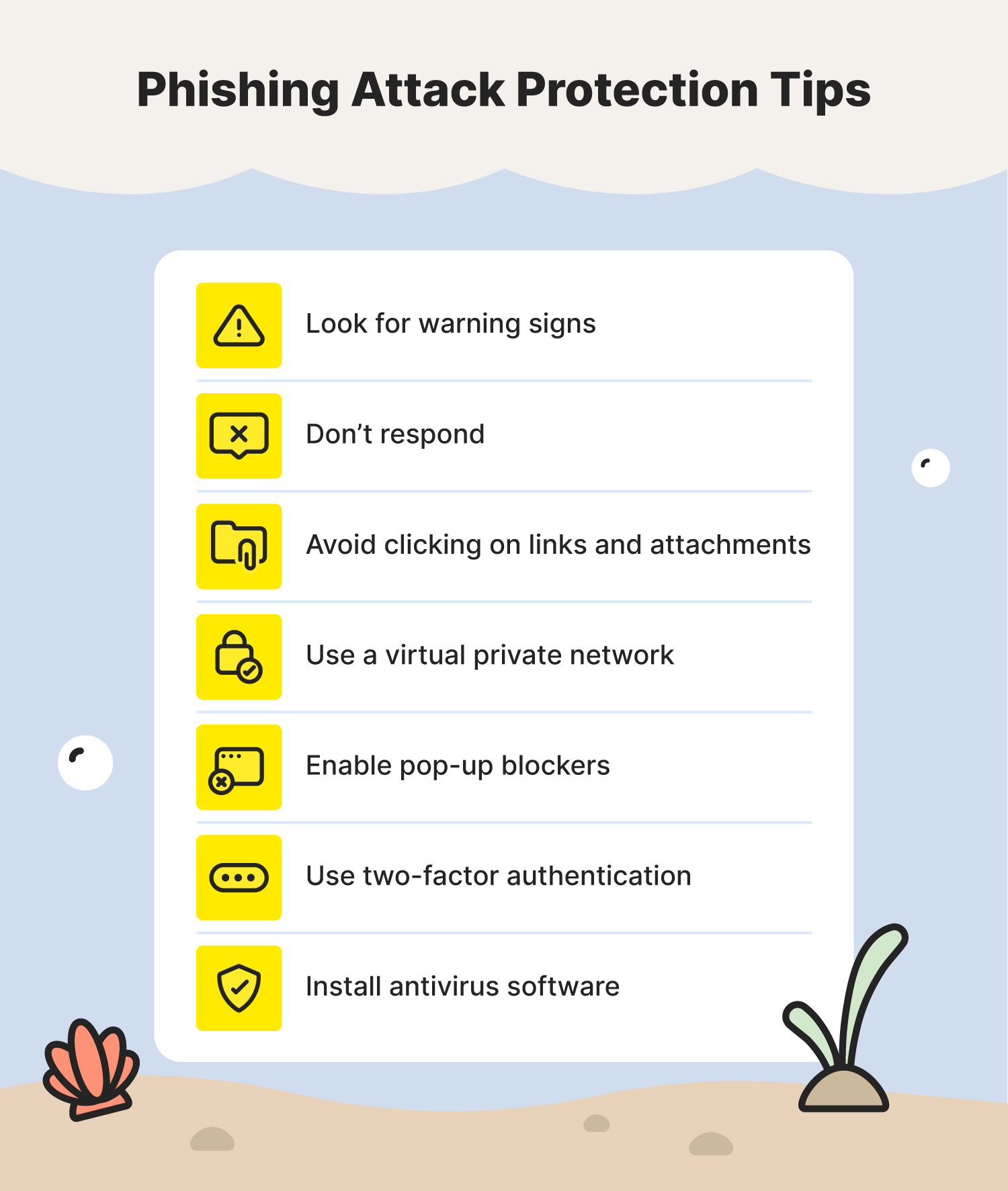
Phishing Warning Email Template Prntbl concejomunicipaldechinu gov co
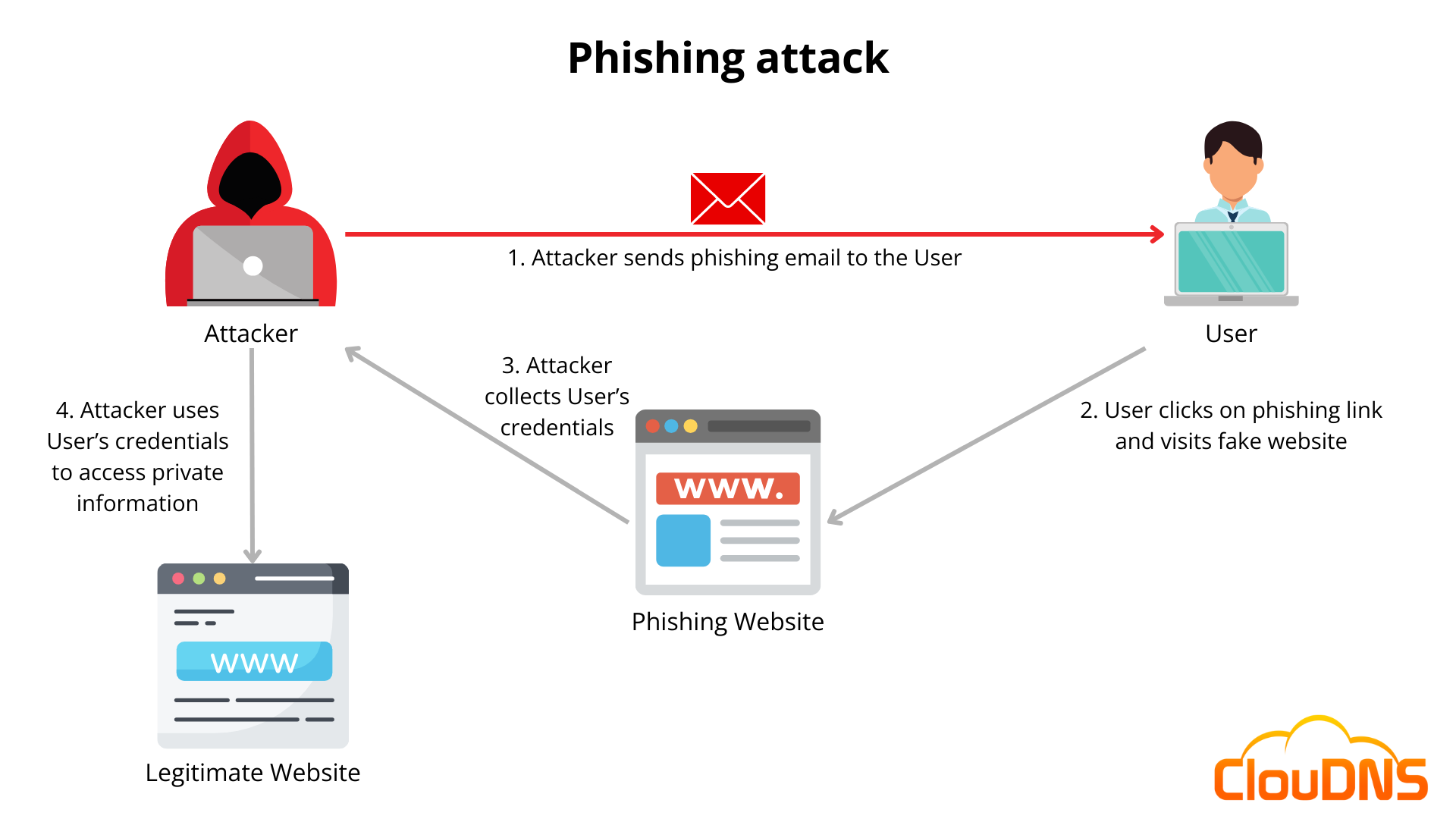
Phishing Attacks